■ Information Security Governance System
The Board of Directors is responsible for reviewing overall information security policies of
E.SUN FHC, as well as important decision-making for issues related to information security.
Risk management committee was established in 2021. The chief information security
officer should report information security issues to risk management committee each year.
Every year, the chairman, president, chief auditor, and the chief officer of the dedicated
information security office shall jointly issue a Declaration of Overall Information Security
Implementation. The Board of Directors and the senior management shall fulfill their duties
of supervision and governance. E.SUN's Board of Directors is comprised of members with
information backgrounds. E.SUN Bank has appointed a chief information security officer
(CISO) to supervise the overall implementation of information security operations, inspect
the effectiveness of information security risk management mechanisms, and report to
the Board of Directors with regard to the overall effectiveness of relevant management
conducted by the information security management organizations. The CISO is the highest
information security officer.
To strengthen information security governance, E.SUN FHC Information Security
Management Committee (ISMC) was set up in 2017. In 2019, the information security
management system of information security unit was established to promote and
implement information security operations. The ISMC is in charge of reviewing E.SUN
FHC Information Security Policy, which is applied to all subsidiaries under E.SUN FHC. In
addition to reviewing governance policy, the Committee also supervises the execution of
information security management and regularly reports to the Board of Directors on the
information security governance status, including policy amendments, risk disclosure and
handling.
E.SUN's vision of information security is to establish a tight and effective information
security defense network. Under this vision, E.SUN gradually improves the comprehensive
protection capacity based on the consistency in information security governance. The aim
is to become a benchmark enterprise of information security governance maturity.
The Information Security Management Division is responsible for FHC's governance,
promotion, and risk management of information security. For information security
governance, it manages a comprehensive governance system, ensures compliance with
regulation, promotes implementation of security procedure, and raises the employees'
awareness and professional abilities of information security. The division utilizes
technologies to identify information security risks and weaknesses, conducts effective
enhancement, establishes a comprehensive governance system and information security
protection capacity and raises employees' information security awareness.
■ Resources for Information Security
E.SUN continuously invests resources in information security-related matters. The expenses spent
in 2020 increased by 48.73% from 2019. Resources were invested to improve the
infrastructure of security governance and technologies, strengthen information security defense
equipment, conduct security intelligence analysis, conduct response drills and provide
education and training, thereby comprehensively improving the Bank's capabilities for
information security
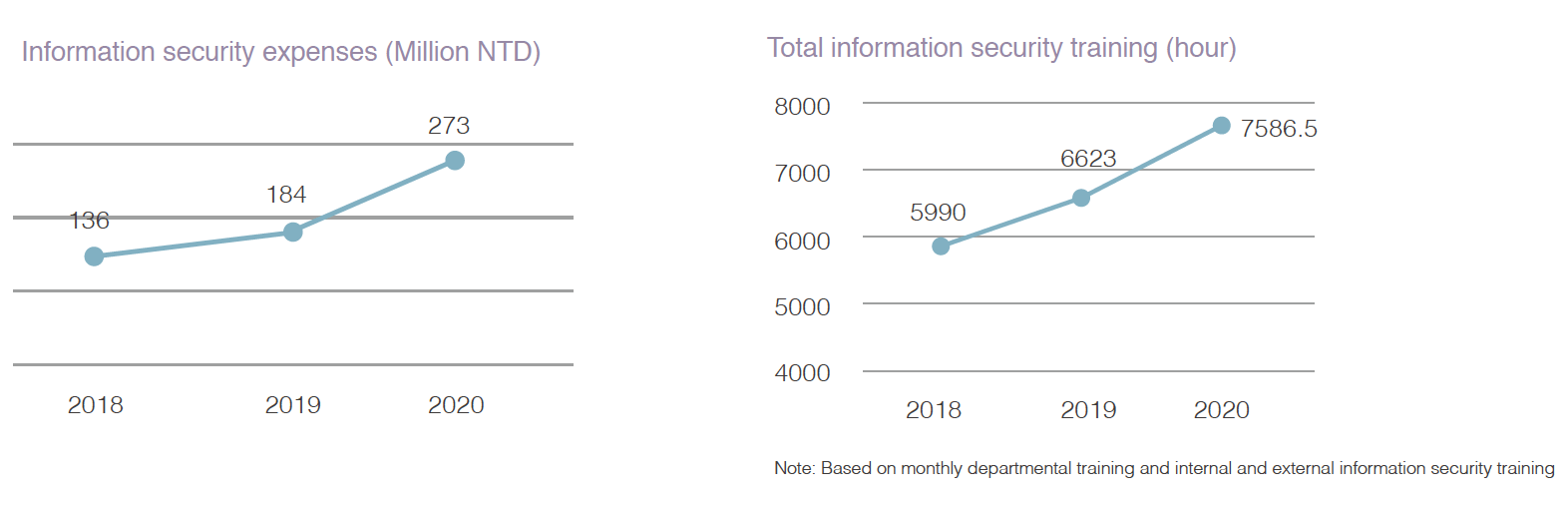
Regarding information security training, 162 employees have obtained
ISO27001 Lead Auditor certification by the end of 2020. All employees in
the Company attended information security tests and the passing rate was
100% in 2020. Additionally, for tech-related personnel, a total of 7,586 hours
of information security courses were conducted, and 93.4% of those were
internal training and 6.6% were external. In addition, the Information Security
Management Division conducts information security training for all employees
every month, and the themes are planned according to the current internal and
external threats.
| Monthly
training of information security in 2020
|
| Month |
Topic |
Month |
Topic |
| January |
Social Engineering Attacks and Prevention
|
July |
Information Security Guide |
| February |
Malware Prevention |
August |
Safety Guide on Mobile Devices |
| March |
Malicious Site Identification |
September |
Protection from Malware |
| April |
Email Attacks |
October |
IT Devices and Physical Safety |
| May |
Information Security for Working form
Home |
November |
Malicious Site Identification |
| June |
IoT's Potential Threat to Information
Security |
December |
Protecting Personal Information
Stored in IT Devices |
■ Information Security Incident
For the reporting and handling of information security incidents, the Company stipulates
the reporting and handling procedures of information security. The information on security
incidents of the entire Bank is recorded by the notification contact of the information
technology unit and ranked by event severity. In major incidents of information security, the
Information Security Management Division and the "notification contact for major incidents of
the FHC/headquarters" must be notified. The Information Security Management Division shall
deal with and solve an information security incident within the target handling time. After the
incident, the root of cause must be analyzed, and corrective measures must be adopted to
prevent any recurrence of incidents.
In the past three years, the information security incidents and the financial losses arising
thereof are shown in the following chart. In the incident in 2020, E.SUN received a customer's
feedback that the customer's internet banking account appeared to have been hacked and
a transfer was conducted. After inspecting the information security equipment and relevant
host computer, it was verified that there was no information security risk such as hacking
or virus infection. The internet banking transaction procedures were also protected by a
comprehensive e-banking transaction security control. The investigation showed that the
customer's cell phone was planted with malware, which caused personal data breach and
usage for account transfers. The incident did not result from internal control faults or major
deficiency in operations. In order to protect the customer's interests, E.SUN compensated
the customer with the full amount and announced the relevant news and alerts on the official
website to remind customers of the risks or improper usage of cell phones.
|
A- Information Security Incident
|
2018 |
2019 |
2020 |
| Total number of information security
incidents |
0 |
0 |
0 |
| Total number of information security
incidents causing customer data loss |
0 |
0 |
0 |
| Total number of customers affected by
information security incidents |
0 |
0 |
0 |
| Financial losses due to information
security incidents |
0 |
0 |
0 |
|
B- Data breaches
|
2018 |
2019 |
2020 |
| Total number of data breaches |
0 |
0 |
0 |
| The percentage of breaches
involving personally identifiable
information |
0% |
0% |
0% |
| Total number of account holders
affected by data breaches involving
personally identifiable information |
0 |
0 |
0 |
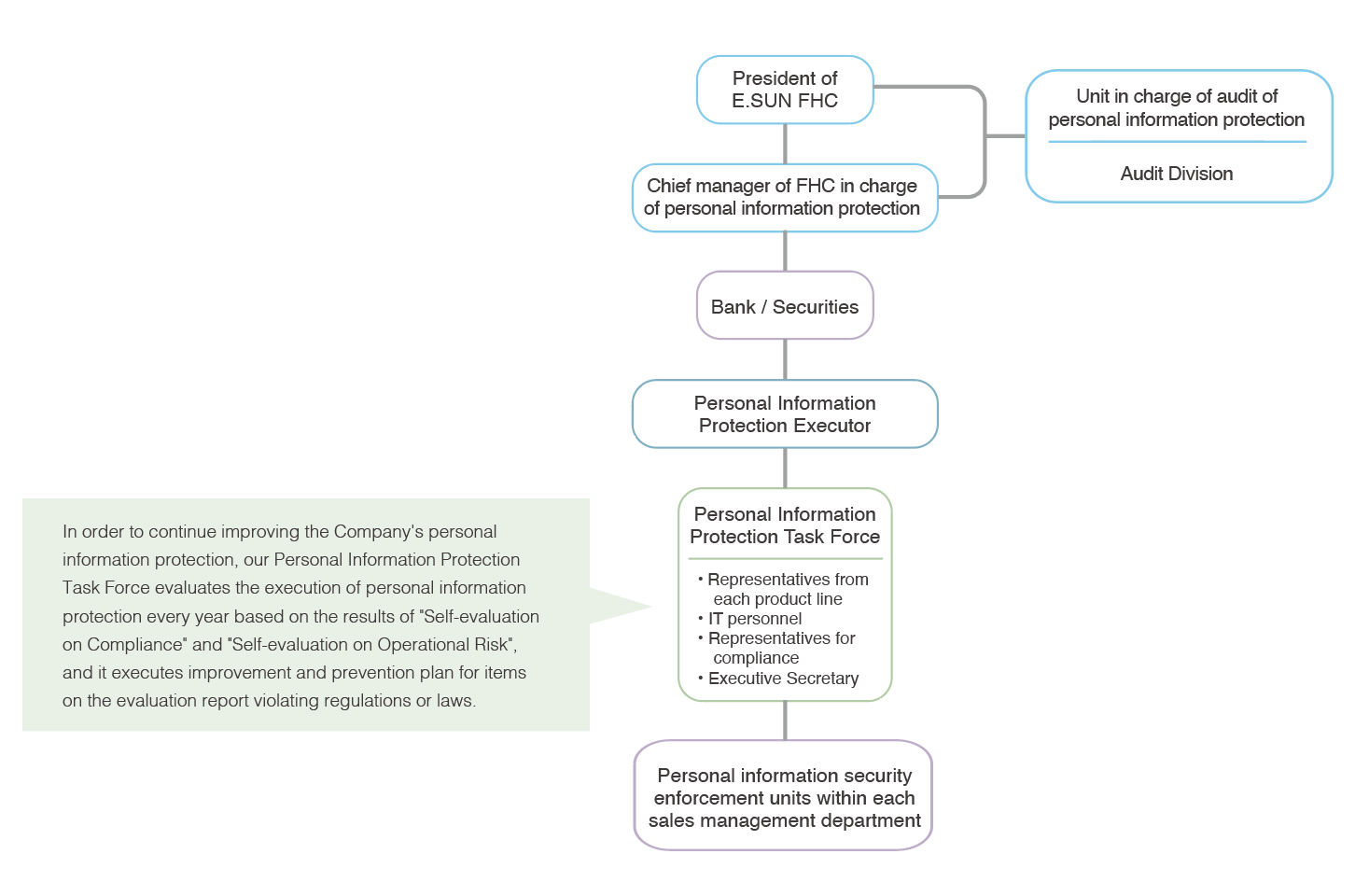
■ Personal Information Protection Management
The Personal Information Protection Task Force is responsible for establishing personal
information protection regulations, which include management measures for collection, handling,
and
use of personal information. The Company followed "E.SUN FHC and Subsidiary Guidelines for
Personal Information Management and Organization" to examine and adjust the Personal File
Checklist and Overview of Corporate Information Flow. The organizational structure is shown in
the chart below.
E.SUN FHC and subsidiaries use customers' data with the utmost care. In 2020, E.SUN
received 36 customer cases relating to personal information; 27 of them came from
the Financial Supervisory Commission and 9 were collected by E.SUN from customer
feedback channels or business units. (Please see the Statistics of the Number of
Complaints Related to E.SUN Services and Personal Information for details.) After
investigating, all cases did not involve personal information breach. However, in one of
the cases, the customer asked for mediation by the Financial Ombudsman Institution and
a compensation of 12,000 NTD was paid. E.SUN always actively responds to customer
complaints and continues to enhance the service staff's training in order to improve E.SUN's
service quality. The 2020 audit was conducted by an independent audit department.
The current status of retained personal information was also reviewed. The audit results
showed that no deficiencies in the use of customer data were found. (Please see the
Statistics of the Number of Audited Deficiency in Terms of the Use of Personal Information
in Recent Years for more details.) E.SUN will persevere in our attempts to protect customer
information.
|
Statistics of the Number of Complaints Related to
E.SUN Services and Personal Information in 2020
|
| Cases of Personal
Information |
Competent
Authority |
Collected by E.SUN |
Total |
| Deposits and transfers |
4 |
1 |
5 |
| Personal credit services |
7 |
2 |
9 |
| Wealth management
services |
9 |
0 |
9 |
| Credit cards services |
5 |
3 |
8 |
| Corporate credit services |
0 |
0 |
0 |
| Other |
2 |
3 |
5 |
| Total |
27 |
9 |
36 |
|
Statistics of the Number of Audited Deficiency in Terms of the Use of Personal
Information in Recent Years
|
| Year |
2016 |
2017 |
2018 |
2019 |
2020 |
| Use of personal information
audited deficiency |
- |
0 |
2 |
0 |
0 |
■ Customer's data for secondary purposes
- I. E.SUN monitors 100% of the usage of customers' data and evaluates whether
processing for another purpose is compatible with the original purpose prior to the
secondary usage. The evaluation principles are as follows:
- (I) Reasonable link between the original and new purposes.
- (II) Whether customers' identities and background are suitable for secondary
usage.
- (III) Nature of the personal data, in particular whether special categories of
sensitive
personal data are processed.
- (IV) The possible consequences of the intended further processing.
- (V) The existence of appropriate safeguards, which may include encryption or
encoding.
- II. The relevant control mechanisms and results of customer's data being used for
secondary purposes are as follows:
- (I) Information processing: All data used are through remote desktop, and the
whole
process is recorded for tracking by the cloud side.
- (II) Data Output: Before the data output, the list review will be conducted
through the
"Global Communication Framework" to exclude customers who are not proper, such
as blacklists, customers who do not accept joint marketing, etc.
|
Cases related to personal
information
|
2019 |
2020 |
| Number of customers' data being
used for secondary purposes |
5.08 million |
7.18 million |
| Percentage of all customers |
74.7% |
76.6% |

